架构图: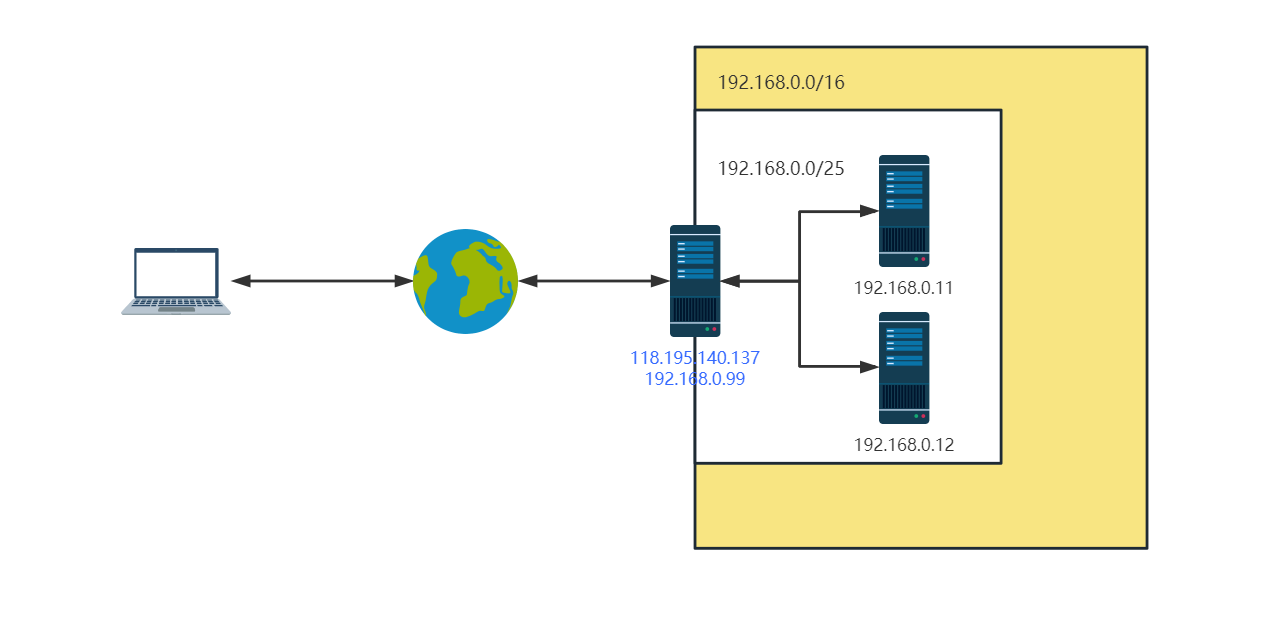
实战目的:通过openvpn连接内网服务器
1、购买服务器
需要一台server和两台web服务器,server服务器必须要外网,其他两台不需要,先买server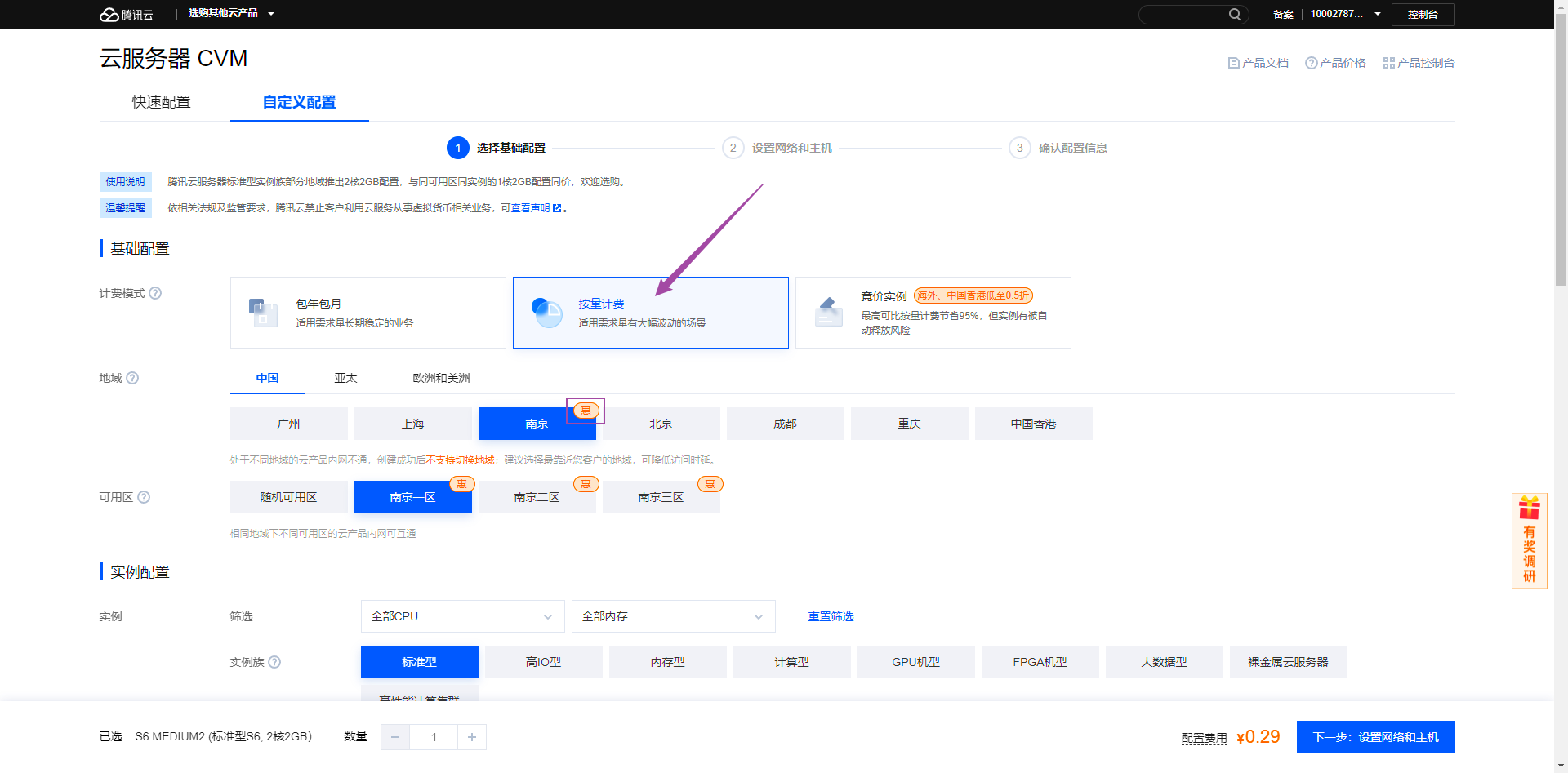
在网络配置环节需要创建私网,可以模仿我,私网范围是192.168.0.0/16,而我们默认使用的是这个私网范围内的子网192.168.0.0/25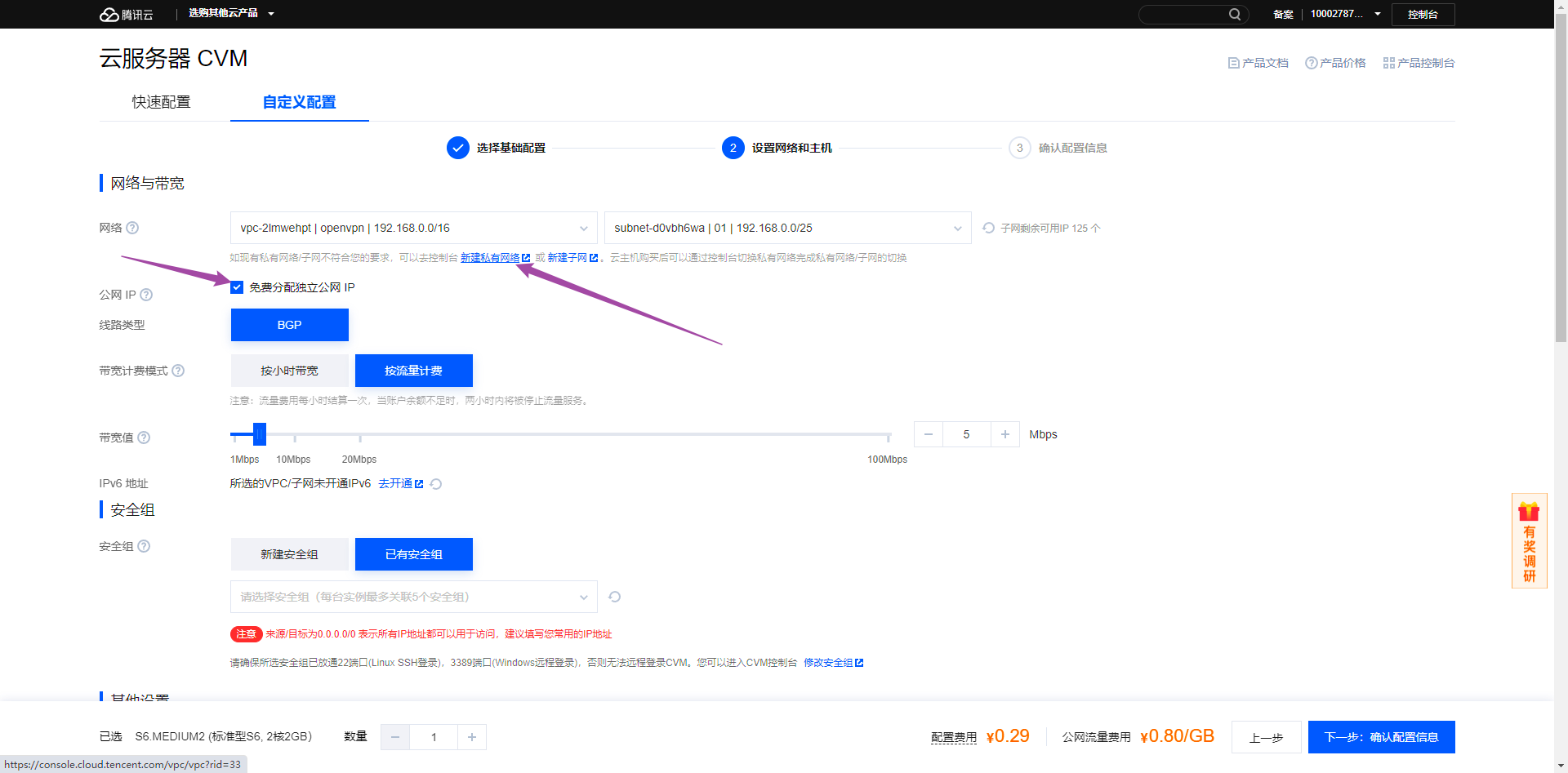
设置好名称和密码即可
然后再买两台web服务器,操作都一样,数量加一台即可,而且不需要公网IP
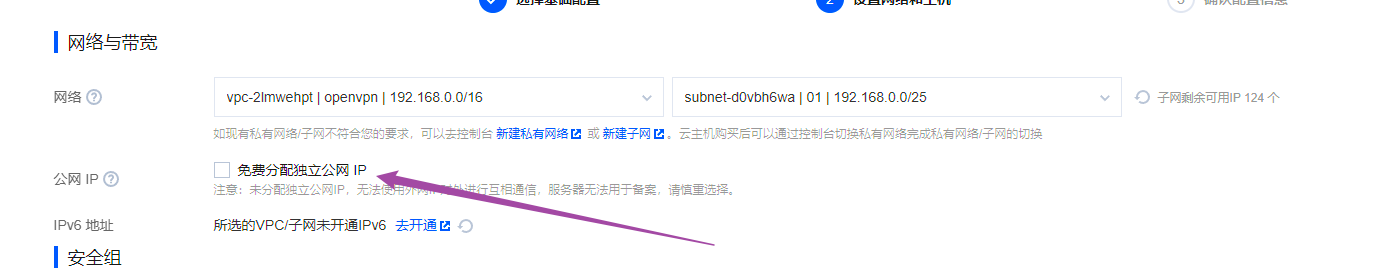
购买完成后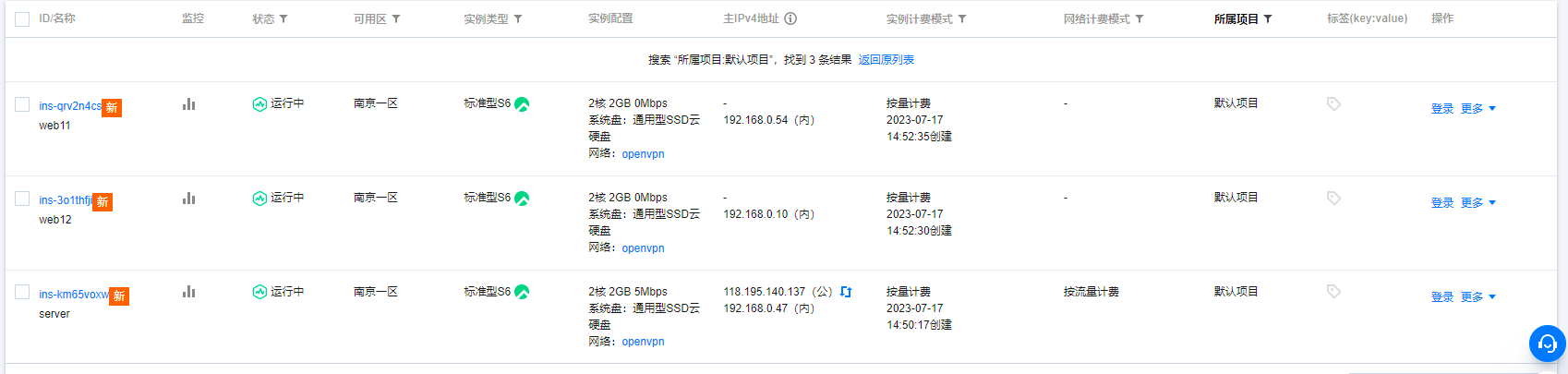
2、调整网络
我们看到现在的私网地址很乱,我们打算把server的地址换成192.168.0.99,其他两台web服务器换成192.168.0.11和192.168.0.12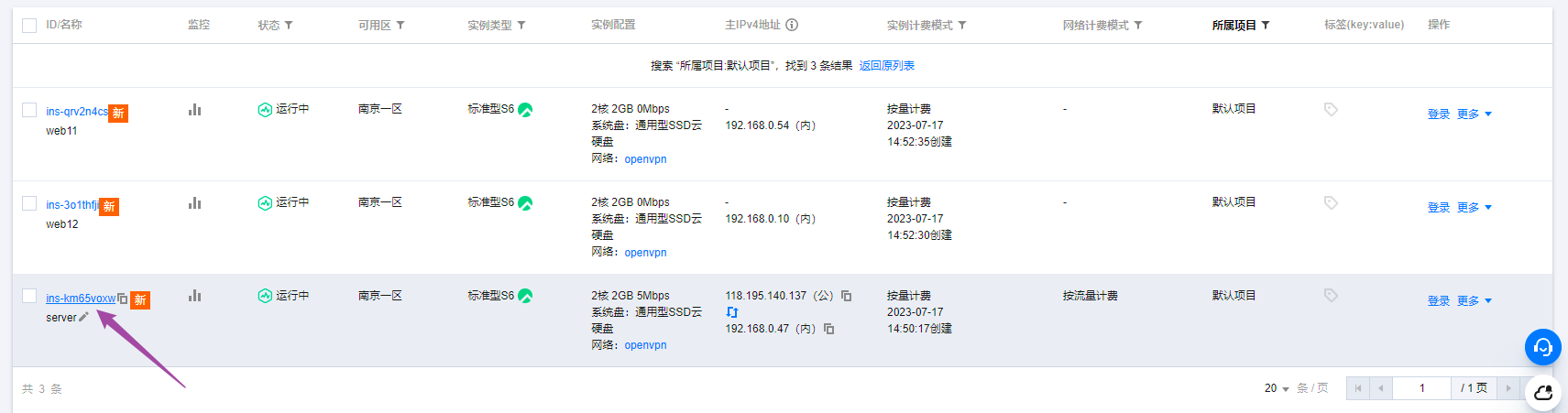
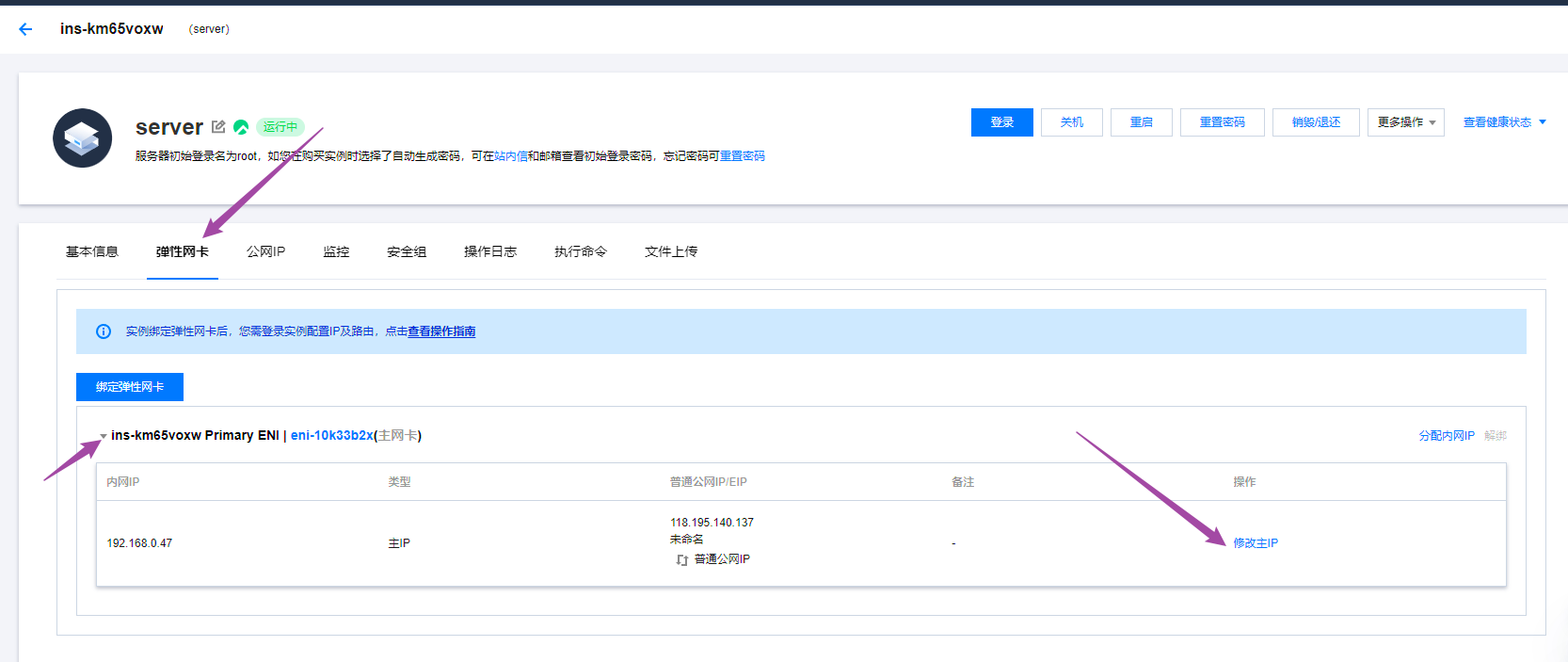
其他两台也按照此操作修改IP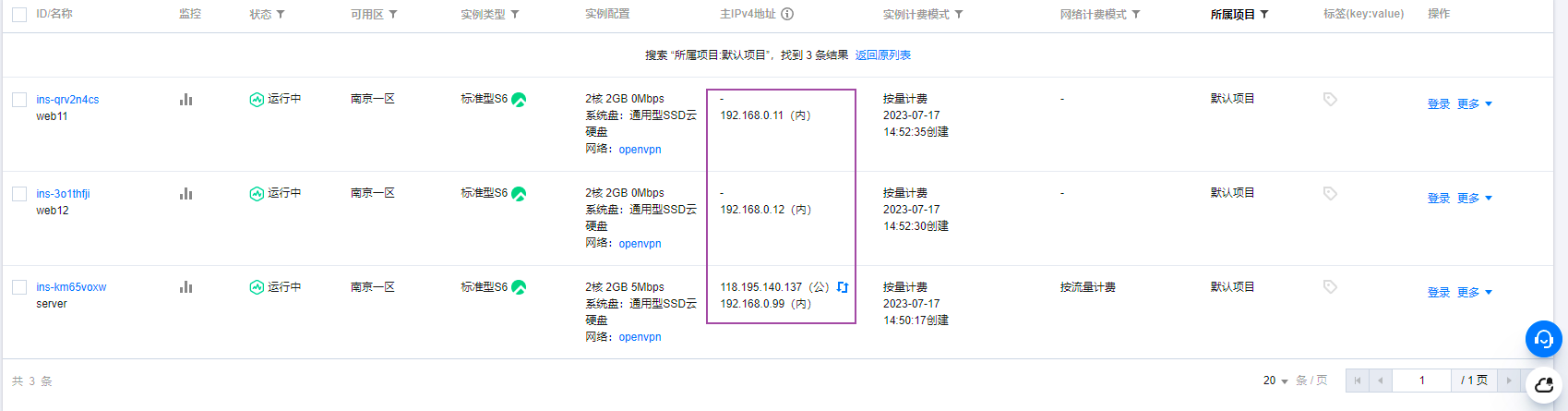
3、web服务器提供web服务
在两台web服务器中安装好nginx并且默认页面显示服务器的主机名,使用一下代码修改主机名(web12记得换)
hostnamectl set-hostname web11rebootyum install -y nginxsystemctl enable --now nginx hostname > /usr/share/ngin/html/index.html4、server服务器安装软件
yum install -y https://mirrors.aliyun.com/epel/epel-release-latest-8.noarch.rpmsed -i \'s|^#baseurl=https://download.example/pub|baseurl=https://mirrors.aliyun.com|\' /etc/yum.repos.d/epel*sed -i \'s|^metalink|#metalink|\' /etc/yum.repos.d/epel*yum -y install openvpnyum -y install easy-rsa5、准备相关配置文件
cp -r /usr/share/easy-rsa/3/ /etc/openvpn/easy-rsacp /usr/share/doc/easy-rsa/vars.example /etc/openvpn/easy-rsa/vars修改/etc/openvpn/easy-rsa/vars文件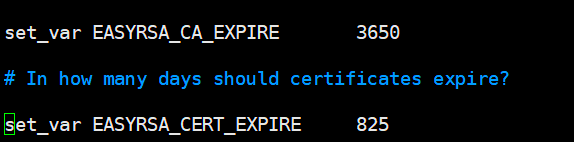
cd /etc/openvpn/easy-rsa/./easyrsa init-pki./easyrsa build-ca nopass./easyrsa gen-req server nopass./easyrsa sign server server./easyrsa gen-dh./easyrsa gen-req web11 nopass./easyrsa sign client web11./easyrsa gen-req web12 nopass./easyrsa sign client web12cp /etc/openvpn/easy-rsa/pki/ca.crt /etc/openvpn/server/cp /etc/openvpn/easy-rsa/pki/issued/server.crt /etc/openvpn/servercp /etc/openvpn/easy-rsa/pki/private/server.key /etc/openvpn/servercp /etc/openvpn/easy-rsa/pki/dh.pem /etc/openvpn/servermkdir /etc/openvpn/client/web11mkdir /etc/openvpn/client/web12find -name "web11*" -exec cp {} /etc/openvpn/client/web11/ \\;find -name "web12*" -exec cp {} /etc/openvpn/client/web12/ \\;cp /etc/openvpn/server/ca.crt /etc/openvpn/client/web11cp /etc/openvpn/server/ca.crt /etc/openvpn/client/web12rm -rf /etc/openvpn/client/web11/web11.reqrm -rf /etc/openvpn/client/web12/web12.reqcp /usr/share/doc/openvpn/sample/sample-config-files/server.conf /etc/openvpn/#删除/etc/openvpn/server.conf中的内容把一下内容复制进去port 1194proto tcpdev tunca /etc/openvpn/server/ca.crtcert /etc/openvpn/server/server.crtkey /etc/openvpn/server/server.keydh /etc/openvpn/server/dh.pemserver 10.8.0.0 255.255.255.0push "route 192.168.0.0 255.255.255.128"keepalive 10 120cipher AES-256-CBCcompress lz4-v2push "compress lz4-v2"max-clients 2048user openvpngroup openvpnstatus /var/log/openvpn/openvpn-status.loglog-append /var/log/openvpn/openvpn.logverb 3mute 20mkdir /var/log/openvpnchown openvpn.openvpn /var/log/openvpn/vim /usr/lib/systemd/system/openvpn@.service[Unit]Description=OpenVPN Robust And Highly Flexible Tunneling Application On %IAfter=network.target[Service]Type=notifyPrivateTmp=trueExecStart=/usr/sbin/openvpn --cd /etc/openvpn/ --config %i.conf[Install]WantedBy=multi-user.targetvim /usr/lib/systemd/system/openvpn@.service[Unit]Description=OpenVPN Robust And Highly Flexible Tunneling Application On %IAfter=network.target[Service]Type=notifyPrivateTmp=trueExecStart=/usr/sbin/openvpn --cd /etc/openvpn/ --config %i.conf[Install]WantedBy=multi-user.targetcp /usr/lib/systemd/system/openvpn@.service /lib/systemd/systemctl enable --now openvpn@server客户端配置
vim /etc/openvpn/client/web11/client.ovpnclientdev tunproto tcpremote 118.195.140.137 1194resolv-retry infinitenobind#persist-key#persist-tunca ca.crtcert web11.crt key web11.keyremote-cert-tls server#tls-auth ta.key 1cipher AES-256-CBCverb 3 compress lz4-v2下载客户端软件
https://openvpn.net/community-downloads/
把客户端的文件打包上传到这
然后连接,绿色标注即为成功
但是还是连接不到内部网络的服务器,只能连接到openvpn的服务器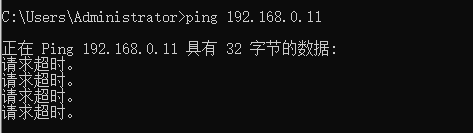
开启转发
sysctl -a | grep ip_forwardvim /etc/sysctl.confnet.ipv4.ip_forward = 1sysctl -piptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j MASQUERADE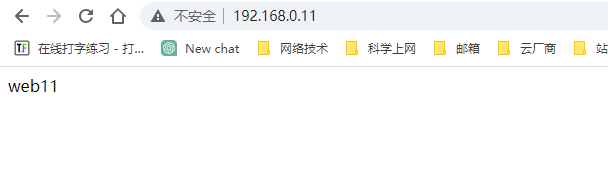

















暂无评论内容